
Did you know that the authentication process in cybersecurity is considered to be one of the weakest links in computer security today?
Authentication is the security process that validates the claimed identity of an entity, relying on one or more characteristics bound to that entity.[1]
The entity in question can be software, firmware, physical devices, or humans. For example, in a website or email system, you are usually identified with a username, and your identity is authenticated when you provide a credential, such as a password, that matches your username in that system’s records. Usernames and passwords are a basic level of authentication.
Authentication is incredibly important in cybersecurity. Permitting only authenticated users (or processes) to access protected resources—computer systems, networks, databases, websites, and more—keeps your network secure.
Adding multiple, different authentication factors to the authentication process typically improves security. It’s fairly common now to see at least two-factor authentication on your bank’s website, or your email account.
It’s estimated that more than 90% of e-commerce sites’ global login traffic comes from hackers trying to break in with stolen usernames and passwords, which is why having strong passwords and good cybersecurity practices is so important.
Have you seen those Facebook quizzes where people share 50 random facts about themselves? You might want to think twice about filling out the next one…
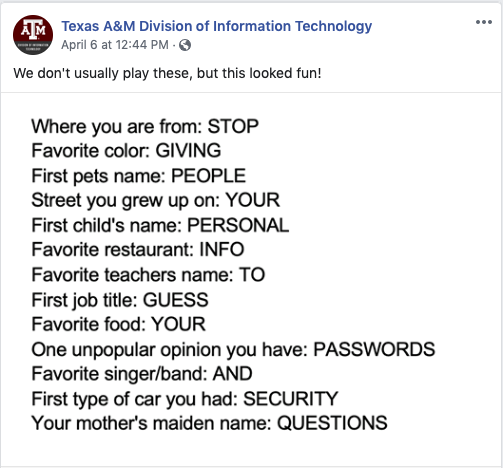
(source)
Understanding the basics of authentication and why it matters will help your employees take your security protocols more seriously. No one wants to be the next Equifax-level breach.
Help them wrap their heads around authentication best practices with interactive microlearning.
One of the newest additions to the eLearning Brothers Off-The-Shelf Courseware is our Cybersecurity Awareness library.
This training course library includes an Authentication bundle covering these topics:
- Authentication: You Need to Know
- Multi-factor Authentication
- Password Management
Our off-the-shelf courses are mobile-friendly and built in a microlearning format. Why microlearning? It’s more engaging and easy for learners to tackle in short bursts.
Our courses are structured around the Rockstar Learning Model™ and follow a Learn, Rehearse, Perform flow. The Rockstar Learning Model is short n’ sweet, fresh, and effective!
Check out our course library and download the full catalog of off-the-shelf courses today.
[1] https://ep.jhu.edu/programs-and-courses/695.712-authentication-technologies








